1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
117
118
119
120
121
122
123
|
[root@logserver01 config]# cat system_login_FromKafkaInES.conf
input{
beats {
host => '172.17.9.200'
port => 5045
}
#
# kafka{
# bootstrap_servers => ["172.17.8.232:6667"]
# topics => ["sys_os_login"]
# codec => "json"
# group_id => "ELK_SYSTEM_LOGIN_GROUP"
# consumer_threads => 3
# client_id => "logstash"
# decorate_events => false
# auto_offset_reset => "earliest"
# request_timeout_ms => "300000"
# session_timeout_ms => "20000"
# max_poll_interval_ms => "600000"
# }
}
filter{
#login successed log
if ([message] =~ "Accepted"){
grok{
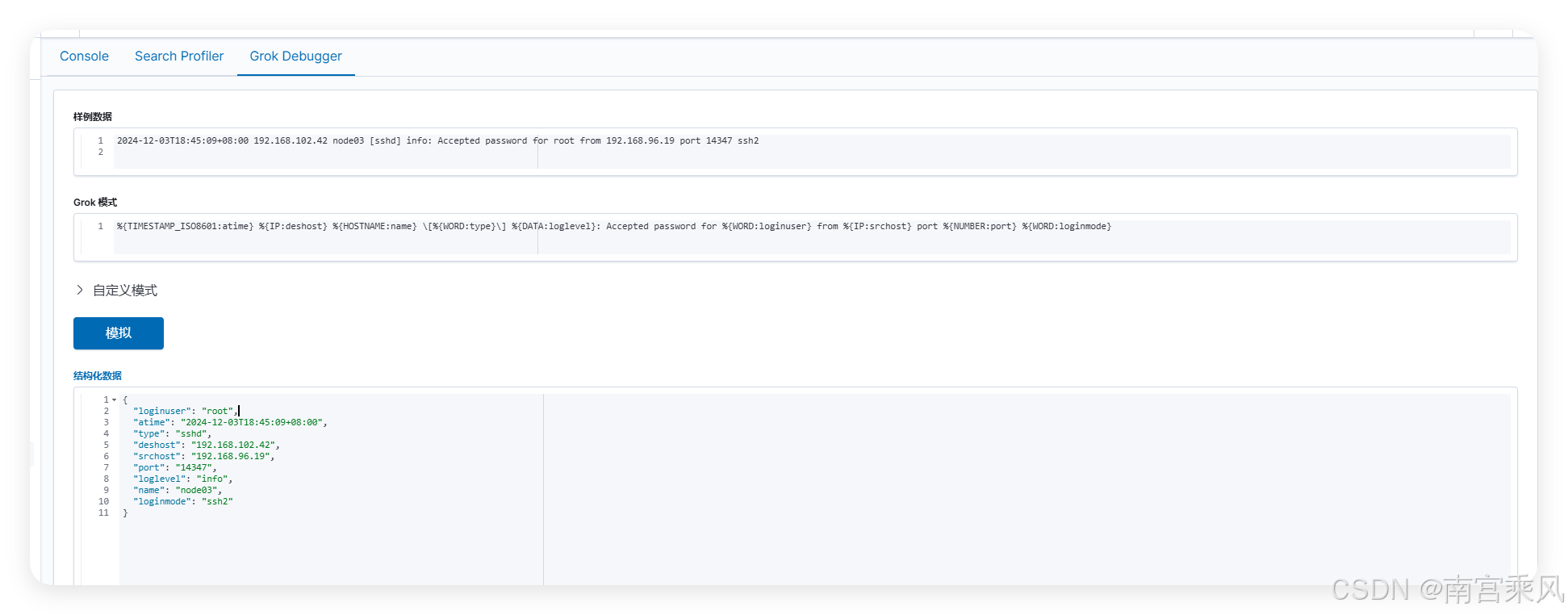
match => {"message" => '^(?<atime>\d+-\d+-\d+)(?:[^\d]+)(?<hhmmss>\d+:\d+:\d+)(?:[^\d]+\d+:\d+)(?:\s+)(?<deshost>\d+\.\d+\.\d+\.\d+)(?:\s)(?<name>[^ ]+)(?:[\S\s]*Failed\spassword\sfor[\sinvalid\suser]*\s)(?<loginuser>[^ ]+)(?:\sfrom\s)(?<srchost>[\d.]+)(?:\s\w+\s\d+\s)(?<loginmode>\w*)'}
}
if "_grokparsefailure" in [tags] { drop { } }
mutate{
add_field => ["type","systemlogin"]
split => ["atime","-"]
}
mutate{
add_field => ["indextime","%{[atime][0]}%{[atime][1]}"]
add_field => ["evtTime","%{[atime][0]}-%{[atime][1]}-%{[atime][2]} %{hhmmss}"]
}
#Retention log insertion time to ES..............
ruby { code => "event.set('inserttime', event.get('@timestamp').time.to_i)" }
#replace InsertTime with evtTime "yyyy-MM-dd HH:mm:ss eg:2020-06-29 09:24:29"
date{
match => ["evtTime","yyyy-MM-dd HH:mm:ss"]
#kibana use this time....................
target => "@timestamp"
}
mutate{replace => ["evtTime","%{evtTime} +0800"]}
date{
match => ["evtTime","yyyy-MM-dd HH:mm:ss +0800"]
timezone =>"UTC"
#log event time timestamp................
target => "logtimestamp"
}
#log event time long string......................
ruby { code => "event.set('longtime', event.get('logtimestamp').time.to_i)" }
mutate{remove_field => [ "evtTime","host","ecs","log","hhmmss","input","agent","atime" ]}
}
#login failed log
else if ([message] =~ "Failed password for"){
grok{
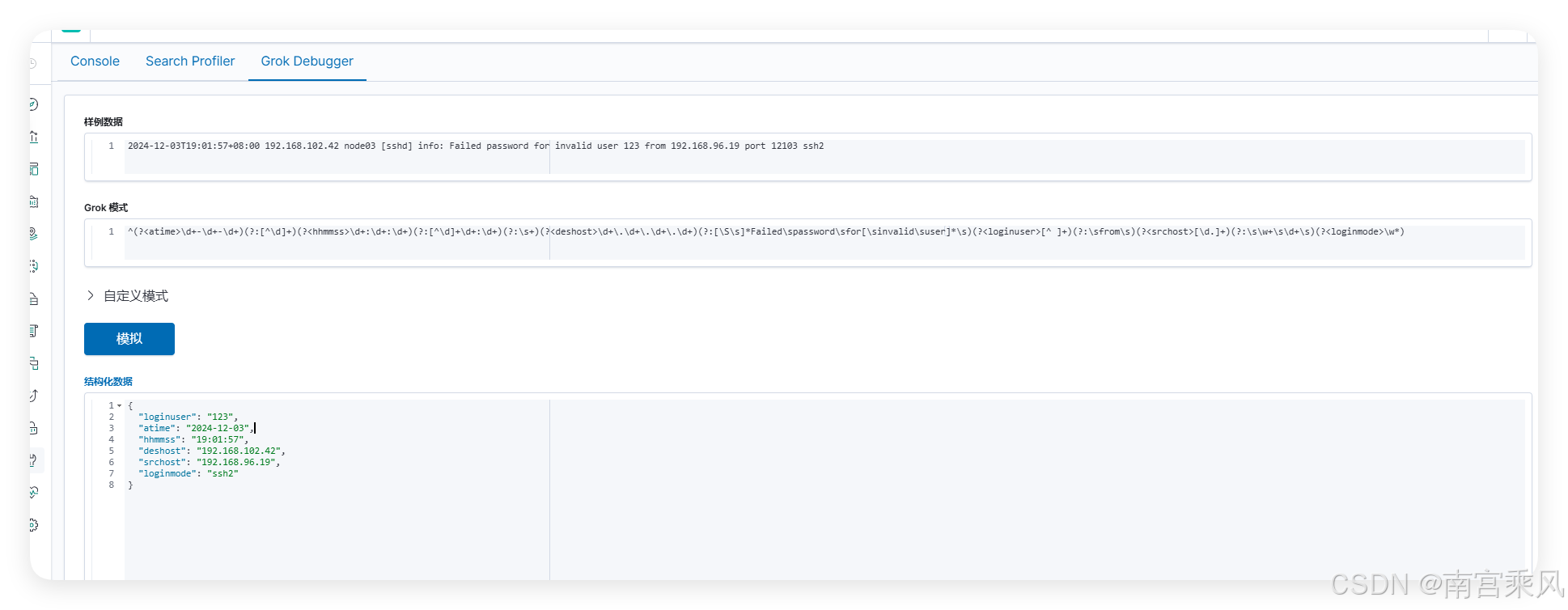
match => {"message" => '^(?<atime>\d+-\d+-\d+)(?:[^\d]+)(?<hhmmss>\d+:\d+:\d+)(?:[^\d]+\d+:\d+)(?:\s+)(?<deshost>\d+\.\d+\.\d+\.\d+)(?:[\S\s]*Failed\spassword\sfor[\sinvalid\suser]*\s)(?<loginuser>[^ ]+)(?:\sfrom\s)(?<srchost>[\d.]+)(?:\s\w+\s\d+\s)(?<loginmode>\w*)'}
}
if "_grokparsefailure" in [tags] { drop { } }
mutate{
add_field => ["type","systemloginfailed"]
split => ["atime","-"]
}
mutate{
add_field => ["indextime","%{[atime][0]}%{[atime][1]}"]
add_field => ["evtTime","%{[atime][0]}-%{[atime][1]}-%{[atime][2]} %{hhmmss}"]
}
#Retention log insertion time to ES..............
ruby { code => "event.set('inserttime', event.get('@timestamp').time.to_i)" }
#replace InsertTime with evtTime "yyyy-MM-dd HH:mm:ss eg:2020-06-29 09:24:29"
date{
match => ["evtTime","yyyy-MM-dd HH:mm:ss"]
#kibana use this time....................
target => "@timestamp"
}
mutate{replace => ["evtTime","%{evtTime} +0800"]}
date{
match => ["evtTime","yyyy-MM-dd HH:mm:ss +0800"]
timezone =>"UTC"
#log event time timestamp................
target => "logtimestamp"
}
#log event time long string......................
ruby { code => "event.set('longtime', event.get('logtimestamp').time.to_i)" }
mutate{remove_field => [ "evtTime","host","ecs","log","hhmmss","input","agent","atime" ]}
}
#other log
else{
drop{}
}
}
output{
if [type] == "systemlogin"{
if [indextime] !~ "index"{
stdout{codec => rubydebug}
elasticsearch{
hosts => "172.17.9.176"
index => "sys_os_systemlogin_%{[indextime]}"
user => "elastic"
password => "f5OPbv6sqfstmc+"
}
}
}
else if [type] == "systemloginfailed"{
if [indextime] !~ "index"{
stdout{codec => rubydebug}
elasticsearch{
hosts => "172.17.9.176"
index => "sys_os_systemloginfailed_%{[indextime]}"
user => "elastic"
password => "xxxxxxx+"
}
}
}
}
|